|
|
The Cisco IOS software supports packet forwarding and routing for ISO CLNS on networks using a variety of data link layers: Ethernet, Token Ring, Fiber Distributed Data Interface (FDDI), and serial. You can use CLNS routing on serial interfaces with High-Level Data Link Control (HDLC), Point-to-Point Protocol (PPP), Link Access Procedure, Balanced (LAPB), X.25, Switched Multimegabit Data Service (SMDS), or Frame Relay encapsulation. To use HDLC encapsulation, you must have a router at both ends of the link. If you use X.25 encapsulation, you must manually enter the network service access point (NSAP)-to-X.121 mapping. The LAPB, X.25, Frame Relay, and SMDS encapsulations interoperate with other vendors.
Cisco's CLNS implementation is also compliant with the Government Open Systems Interconnection Profile (GOSIP) Version 2. As part of its CLNS support, Cisco routers fully support the following ISO and American National Standards Institute (ANSI) standards:
Both the ISO-developed IS-IS routing protocol and Cisco's ISO Interior Gateway Routing Protocol (IGRP) are supported for dynamic routing of ISO CLNS. In addition, static routing for ISO CLNS is supported.
The world of OSI networking has a unique terminology:
Addresses in the ISO network architecture are referred to as NSAP addresses and network entity titles (NETs). Each node in an OSI network has one or more NETs. In addition, each node has many NSAP addresses. Each NSAP address differs from one of the NETs for that node in only the last byte (see Figure 12-1). This byte is called the n-selector. Its function is similar to the port number in other protocol suites.
Cisco's implementation supports all NSAP address formats that are defined by ISO 8348/Ad2; however, Cisco provides dynamic routing (ISO-IGRP or IS-IS routing) only for NSAP addresses that conform to the address constraints defined in the ISO standard for IS-IS (ISO 10589).
An NSAP address consists of two major fields:
The key difference between the ISO-IGRP and IS-IS NSAP addressing schemes is in the definition of area addresses. Both use the system ID for Level 1 routing. However, they differ in the way addresses are specified for area routing. An ISO-IGRP NSAP address includes three separate levels for routing: the domain, area, and system ID. An IS-IS address includes two fields: a single continuous area field comprising the domain and area fields defined for ISO-IGRP and the system ID.
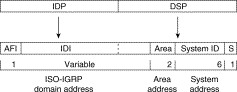
Figure 12-1 illustrates the ISO-IGRP NSAP addressing structure.

The ISO-IGRP NSAP address is divided into three parts: a domain part, an area address, and a system ID. Domain routing is performed on the domain part of the address. Area routing for a given domain uses the area address. System ID routing for a given area uses the system ID part. The NSAP address is laid out as follows:
Our ISO-IGRP routing implementation interprets the bytes from the AFI up to (but not including) the area field in the DSP as a domain identifier. The area field specifies the area, and the system ID specifies the system.
Figure 12-2 illustrates the IS-IS NSAP addressing structure.
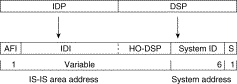
An IS-IS NSAP address is divided into two parts: an area address (AA) and a system ID. Level 2 routing uses the AA. Level 1 routing uses the system ID address. The NSAP address is laid out as follows:
The IS-IS routing protocol interprets the bytes from the AFI up to (but not including) the system ID field in the DSP as an area identifier. The system ID specifies the system.
All NSAP addresses must obey the following constraints:
The following are examples of OSI network and GOSIP NSAP addresses using the ISO-IGRP implementation. The second example is the OSI network NSAP address format:
47.0004.004D.0003.0000.0C00.62E6.00|Domain|Area|System ID|S|
Routes are entered by specifying pairs (NSAP prefix and next-hop NET). NETs are similar in function to NSAP addresses. In the routing table, the best match means the longest NSAP prefix entry that matches the beginning of the destination NSAP address. In Table 12-1, which is an example of a static routing table, the next-hop NETs are listed for completeness but are not necessary to understand the routing algorithm. Table 12-2 offers examples of how the longest matching NSAP prefix can be matched with routing table entries in Table 12-1 .
| Entry | NSAP Address Prefix | Next-Hop NET |
1 | | |
2 | | |
3 | | |
4 | | |
5 | | |
| Datagram Destination NSAP Address | Table Entry Number Used |
| 1 |
| 1 |
| 2 |
| 3 |
| 4 |
| 5 |
Octet boundaries must be used for the internal boundaries of NSAP addresses and NETs.
This section presents protocol-related troubleshooting information for ISO CLNS protocol connectivity and performance problems. It describes specific ISO CLNS symptoms, the problems that are likely to cause each symptom, and the solutions to those problems.
The following sections cover the most common network issues in ISO CLNS networks:
Symptom: Hosts cannot communicate with other hosts. Hosts might be located on the local or a remote network. Connections to some hosts on a network might be possible, whereas connections to other hosts on the same network fail.
Table 12-3 outlines the problems that might cause this symptom and describes solutions to those problems.
| Possible Problem | Solution |
|---|---|
Step 1 Determine whether a default gateway is specified in the adjacency table of the host attempting to make a connection. Use the following UNIX command: host% netstat -rn Check the output of this command for a default gateway specification. Syntax Description:
Step 2 If the default gateway specification is incorrect, or if it is not present at all, you can change or add a default gateway using the following UNIX command at the local host: host% route add default address 1 where address is the IP address of the default gateway (the router local to the host). The value 1 indicates that the specified gateway is one hop away. Step 3 It is recommended that you specify a default gateway as part of the boot process. Specify the ISO CLNS address of the gateway in the following UNIX host file: /etc/defaultrouter This filename might be different on your UNIX system. | |
Step 1 Use the show clns neighbors detail privileged exec command to show all ESs2 and ISs3 to which the router is directly connected. Step 2 Make sure there is at least one Level 1 router on the same network as the end system. | |
Step 1 Verify that the Level 1 router has the same address as the ES. Step 2 Verify that all bytes of the NSAP4 address, up to but not including the system ID, are the same on both the router and the ES. The domain and area addresses must match, and the station IDs must be unique. (The value of the n-selector byte has no impact in this case.) | |
ES host is not running ES-IS5 protocol | Step 1 Use the appropriate host commands to verify that an ES-IS process is running. If necessary, initiate the ES-IS process on the host. Step 2 Check the adjacency database on the host and verify that it has an entry for its directly connected router. Step 3 Use the debug clns packet privileged exec command on the Level 1 router to verify that it sees and forwards packets from the ES. Caution: Because debugging output is assigned high priority in the CPU process, it can render the system unusable. For this reason, use debug commands only to troubleshoot specific problems or during troubleshooting sessions with Cisco technical support staff. Moreover, it is best to use debug commands during periods of lower network traffic and fewer users. Debugging during these periods decreases the likelihood that increased debug command processing overhead will affect system use. Step 4 If necessary, statically configure the router to recognize the ES by using the clns es-neighbor interface configuration command. The following is the syntax for the clns es-neighbor command: clns es-neighbor nsap snpa Syntax Description:
Example: The following example defines an ES neighbor on Ethernet interface 0: interface ethernet 0 clns es-neighbor 47.0004.004D.0055.0000.0C00.A45B.00 0000.0C00.A45B In this case, the end systems with the following NSAP, or NET7, are configured with an Ethernet MAC address of 0000.0C00.A45B:
|
Step 1 Use the trace exec command to check connectivity between routers and the source ES. Step 2 If the trace fails at a router, use the show clns neighbors exec command to see which neighboring routers and ESs are recognized. Sample Display: The following is sample output from the show clns neighbors command. This display is a composite of the show clns es-neighbor and show clns is-neighbor commands: router# show clns neighbors System Id SNPA Interface State Holdtime Type Protocol 0000.0000.0007 aa00.0400.6408 Ethernet0 Init 277 IS ES-IS 0000.0C00.0C35 0000.0c00.0c36 Ethernet1 Up 91 L1 IS-IS 0800.2B16.24EA aa00.0400.2d05 Ethernet0 Up 29 L1L2 IS-IS 0800.2B14.060E aa00.0400.9205 Ethernet0 Up 1698 ES ES-IS 0000.0C00.3E51 *HDLC* Serial1 Up 28 L2 IS-IS 0000.0C00.62E6 0000.0c00.62e7 Ethernet1 Up 22 L1 IS-IS 0A00.0400.2D05 aa00.0400.2d05 Ethernet0 Init 24 IS ES-IS Step 3 If neighboring routers and end systems are up, perform one of the following procedures:
| |
Route redistribution problem | Misconfigured route redistribution can cause connectivity problems. For specific troubleshooting information, see the section "ISO CLNS: Redistribution Causes Routing Problems" later in this chapter. |
Symptom: Hosts cannot access other hosts in the same area. The hosts might be on the same network or they might be in a different network in the same area.
Table 12-4 outlines the problems that might cause this symptom and describes solutions to those problems.
| Possible Problem | Solution |
|---|---|
Step 1 Check all Level 1 routing tables and link-state databases. Step 2 Verify that the hosts are in the same area. Step 3 Check that the NSAP address is entered correctly on the hosts. | |
Different area addresses are merged into a single area, but the router is configured incorrectly | Step 1 Use the show running-config privileged exec command to see router configurations. Check whether multiple area addresses are configured.
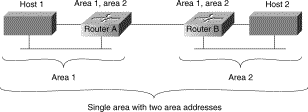
Step 2 If multiple network addresses are configured, verify that the router is configured to support a multihomed area Step 3 To communicate, routers must establish a Level 1 adjacency. Therefore, area addresses in a multihomed area must overlap across routers. For example, in the multihomed area shown in Figure 12-3, to configure Area 1 and Area 2 as a multihomed area, both Router A and Router B must be configured to be in both areas. IS-IS routing supports the assignment of multiple area addresses on the same router. This concept is referred to as multihoming. Multihoming provides a mechanism for smoothly migrating network addresses, as follows:
|
Different area addresses are merged into a single area, but the router is configured incorrectly |
You must statically assign the multiple area addresses on the router. Cisco currently supports assignment of up to three area addresses on a router. The number of areas allowed in a domain is unlimited. All the addresses must have the same system ID. For example, you can assign one address (area1 plus system ID) and two additional addresses in different areas (area2 plus system ID and area3 plus system ID) where the system ID is the same. Step 4 Alternatively, one router can be configured in both areas, while the other router remains configured for a single area. Provided that the area numbers on routers overlap, the routers will establish a Level 1 adjacency, allowing them to communicate. |
Step 1 Use the appropriate host commands to verify that an ES-IS process is running. If necessary, initiate the ES-IS process on the host. Step 2 Check the adjacency database on the host and verify that it has an entry for its directly connected router. Step 3 Use the debug clns packet privileged exec command on the Level 1 router to verify that it sees and forwards packets from the ES. | |
ES host is not running | Caution: Because debugging output is assigned high priority in the CPU process, it can render the system unusable. For this reason, use debug commands only to troubleshoot specific problems or during troubleshooting sessions with Cisco technical support staff. Moreover, it is best to use debug commands during periods of lower network traffic and fewer users. Debugging during these periods decreases the likelihood that increased debug command processing overhead will affect system use. Step 4 If necessary, statically configure the router to recognize the ES by using the clns es-neighbor interface configuration command. The following is the syntax for the clns es-neighbor command: clns es-neighbor nsap snpa Syntax Description:
Example: The following example defines an ES neighbor on Ethernet interface 0: interface ethernet 0 clns es-neighbor 47.0004.004D.0055.0000.0C00.A45B.00 0000.0C00.A45B |
Route redistribution problem | Misconfigured route redistribution can cause connectivity problems. For specific troubleshooting information, see the section "ISO CLNS: Redistribution Causes Routing Problems" later in this chapter. |
Symptom: Host cannot access hosts in a different area. Hosts in the same area are accessible.
Table 12-5 outlines the problems that might cause this symptom and describes solutions to those problems.
| Possible Problem | Solution |
|---|---|
Step 1 Use the trace command to verify that Level 1 routers are routing packets to the nearest Level 2 router. Sample Display: The following display shows an example of ISO CLNS trace output:
| |
| Step 2 Use the trace exec command to verify that Level 2 routers are routing packets to the correct destination area. Step 3 If packets are not being routed to the correct area, check the Level 2 routing tables (ISO-IGRP1) or the Level 2 link state databases (IS-IS) to see whether the packets are being forwarded to another area. Step 4 If necessary, reconfigure routers with the correct area addresses and Level 2 (IS-IS) routing information. |
Step 1 Use the appropriate host commands to verify that an ES-IS process is running. If necessary, initiate the ES-IS process on the host. Step 2 Check the adjacency database on the host and verify that it has an entry for its directly connected router. Step 3 Use the debug clns packet privileged exec command on the Level 1 router to verify that it sees and forwards packets from the ES. Caution: Because debugging output is assigned high priority in the CPU process, it can render the system unusable. For this reason, use debug commands only to troubleshoot specific problems or during troubleshooting sessions with Cisco technical support staff. Moreover, it is best to use debug commands during periods of lower network traffic and fewer users. Debugging during these periods decreases the likelihood that increased debug command processing overhead will affect system use. Step 4 If necessary, statically configure the router to recognize the ES by using the clns es-neighbor interface configuration command. | |
Route redistribution problem | Misconfigured route redistribution can cause connectivity problems. For specific troubleshooting information, see the section "ISO CLNS: Redistribution Causes Routing Problems" later in this chapter. |
Step 1 Use the trace exec command to check connectivity between routers and the source ES. Sample Display: The following display shows an example of ISO CLNS trace output:
Step 2 If the trace fails at a router, use the show clns neighbors exec command to see which neighboring routers and ESs are recognized. Step 3 If neighboring routers and end systems are up, perform one of the following procedures:
|
| 1IGRP = Interior Gateway Routing Protocol 2LSP = Link State Protocol |
Symptom: Host connections fail using certain protocols. Hosts might be able to connect to other hosts using some protocols but are unable to connect using others.
Table 12-6 outlines the problems that might cause this symptom and describes solutions to those problems.
| Possible Problem | Solution |
|---|---|
Verify that the needed protocols are correctly installed and configured on the host system. Consult your vendor's documentation for information on configuring hosts. | |
Step 1 Use the trace exec command to determine the path taken to reach remote hosts. Step 2 If you discover a router that is stopping traffic, use the show access-lists privileged exec command to see whether any access lists are configured on the router. Step 3 Disable all access lists on the router using no access-group interface configuration commands on the appropriate interfaces. Step 4 Determine whether hosts can now use the protocol in question. If traffic can get through, it is likely that an access list is blocking protocol traffic. Step 5 Make sure the access list does not filter traffic from ports that are used by the protocol in question. Configure explicit permit statements for traffic that you want the router to forward normally. Step 6 Enable the access list and verify that the protocol still functions correctly. If problems persist, continue isolating and analyzing access lists on all routers in the path from source to destination. |
Symptom: In environments with multiple paths between networks, when one link goes down, connections across a parallel link are not possible.
Table 12-7 outlines the problems that might cause this symptom and describes solutions to those problems.
| Possible Problem | Solution |
|---|---|
Step 1 Use the show clns route privileged exec command to view the CLNS routing table. Examine the table for routes listed as "possibly down." This indicates that the routing protocol has not converged. Step 2 Wait for the routing protocol to converge. Use the show clns route command again to see whether the routes are now up. Note: ISO-IGRP does load balancing only for domain prefix routes. If you are doing Level 1 or Level 2 routing in ISO-IGRP, only a single path is maintained. If that path goes down, you must wait for the network to converge before the alternate path is available. | |
Step 1 Use the trace exec command to determine the path taken to reach remote hosts. Step 2 If you discover a router that is stopping traffic, use the show access-lists privileged exec command to see whether any access lists are configured on the router. Step 3 Disable all access lists on the router using no access-group interface configuration commands on the appropriate interfaces. Step 4 Determine whether hosts can now use the protocol in question. If traffic can get through, it is likely that an access list is blocking protocol traffic. Step 5 Make sure the access list does not filter traffic from ports that are used by the protocol in question. Configure explicit permit statements for traffic that you want the router to forward normally. Step 6 Enable the access list and verify that the protocol still functions correctly. If problems persist, continue isolating and analyzing access lists on all routers in the path from source to destination. | |
Hardware or | For information on troubleshooting hardware problems, see "Troubleshooting Hardware and Booting Problems." For information on troubleshooting media problems, refer to the media troubleshooting chapter that covers the media type used in your network. |
Symptom: Route redistribution does not work properly and causes routing problems. Traffic does not get through a router that is redistributing routes between two different routing areas or domains---typically IS-IS and ISO-IGRP. Observed symptoms range from poor performance to no communication at all.
Table 12-8 outlines the problems that might cause this symptom and describes solutions to those problems.
| Possible Problem | Solution |
|---|---|
The sequence numbers used in route-map router configuration commands determine the order in which conditions are tested. Misordered sequence numbers can cause redistribution problems. Step 1 Use the show running-config privileged exec command to display the router configuration. Look for route-map router configuration command entries. Step 2 If route-map commands are configured, look at the sequence numbers that are assigned. Lower sequence numbers are tested before higher sequence numbers, regardless of the order in which they are listed in the configuration. Step 3 If conditions are not being tested in the order you want, you must modify the sequence numbers to change the testing order. The syntax for the route-map command to adjust the sequence number is as follows: route-map map-tag {permit | deny} sequence-number Syntax Description:
| |
Misordered sequence |
|
Step 1 Use the show running-config exec command to view the router configuration. Look for a default-metric router configuration command entry. Step 2 If the default-metric router configuration command or the distance router configuration command is missing, add the appropriate version of the missing command. Syntax: The following is the syntax for the default-metric command: default-metric number Syntax Description:
Syntax: The following is the syntax for the distance command: distance value [clns] Syntax Description:
Refer to the Cisco IOS Network Protocols Configuration Guide, Part 2 and Network Protocols Command Reference, Part 2 for information about adjusting ISO CLNS default metrics. | |
Step 1 Use the show running-config exec command to view the router configuration. Look for a distance router configuration command entry. Step 2 If the distance command is missing, configure a distance specification on the router. Use the distance router configuration command to configure the administrative distance for CLNS routes learned. Syntax: The following is the syntax for the distance command: distance value [clns] Syntax Description:
Example: In the following example, the distance value for CLNS routes learned is 90. Preference is given to these CLNS routes rather than routes with the default administrative distance value of 110: router isis distance 90 clns | |
Redistribution between an IS-IS cloud and an ISO-IGRP cloud should be performed only at a single point. If it is not, routing information can be advertised back into one of the clouds, causing routing feedback loops. Examples: The following example illustrates redistribution of ISO-IGRP routes of Michigan and ISO-IGRP routes of Ohio into the IS-IS area tagged USA: router isis USA redistribute iso-igrp Michigan redistribute iso-igrp Ohio The following example illustrates redistribution of IS-IS routes of France and ISO-IGRP routes of Germany into the ISO-IGRP area tagged Backbone: router iso-igrp Backbone redistribute isis France redistribute iso-igrp Germany If you must redistribute at another point, use default metrics to perform the redistribution in one direction only. Refer to the Cisco IOS Network Protocols Configuration Guide, Part 2 and Network Protocols Command Reference, Part 2 for information about adjusting ISO CLNS default metrics. |
Symptom: Users experience poor performance or sudden loss of connections. One or more routers might be receiving duplicate routing updates and might see routers and ESs on multiple interfaces.
Table 12-9 outlines the problems that might cause this symptom and describes solutions to those problems.
| Possible Problem | Solution |
|---|---|
Multiple ISO-IGRP |
Step 2 If multiple ISO-IGRP processes are configured on a single interface, different Level 2 updates are being sent out through the same interface. Multiple Level 2 updates on the same interface can cause congestion problems, especially if the network is large and links are flapping outside the damping intervals. Flapping is a routing problem where an advertised route between two nodes alternates (flaps) back and forth between two paths due to a network problem that causes intermittent interface failures. Step 3 Remove one of the ISO-IGRP processes from the interface configuration using the appropriate no clns router iso-igrp interface configuration command. |
A bridge or repeater in parallel with a router can cause updates and traffic to be seen from both sides of an interface. Step 1 Use the show clns is-neighbors detail and the show clns neighbors detail exec commands to see through which routers and protocols the router's adjacencies were learned. | |
The following is sample output from the show clns neighbors detail command: router# show clns neighbors detail System Id SNPA Interface State Holdtime Type Protocol 000.0000.0007 aa00.0400.6408 Ethernet0 Init 291 IS ES-IS Area Address(es): 47.0005.80FF.F500.0000.0003.0020 0000.0C00.0C35 0000.0c00.0c36 Ethernet1 Up 94 L1 IS-IS Area Address(es): 47.0004.004D.0001 39.0001 0800.2B16.24EA aa00.0400.2d05 Ethernet0 Up 9 L1L2 IS-IS Area Address(es): 47.0004.004D.0001 0800.2B14.060E aa00.0400.9205 Ethernet0 Up 1651 ES ES-IS Area Address(es): 49.0040 0000.0C00.3E51 *HDLC* Serial1 Up 27 L2 IS-IS Area Address(es): 39.0004 0000.0C00.62E6 0000.0c00.62e7 Ethernet1 Up 26 L1 IS-IS Area Address(es): 47.0004.004D.0001 oA00.0400.2D05 aa00.0400.2d05 Ethernet0 Init 29 IS ES-IS Area Address(es): 47.0004.004D.0001 Look for routers that are known to be on a remote network. A router listed in the adjacency table but that is not on a directly connected network indicates a problem. You can also look for paths to networks (or areas) on multiple interfaces. Step 2 If you determine that there is a parallel bridge or repeater, remove the device or configure filters that block routing updates from being learned from the device. | |
Route redistribution | Misconfigured route redistribution can cause performance problems. For specific troubleshooting information, see the section "ISO CLNS: Redistribution Causes Routing Problems" earlier in this chapter. |
Posted: Tue May 16 15:08:04 PDT 2000
Copyright 1989 - 2000©Cisco Systems Inc.